SMS one-time passwords are becoming one of the weakest links in user authentication. They fail frequently, slow users down, and expose businesses to SIM swap fraud, phishing, and social engineering. Many organizations are now looking for a modern alternative that is faster, more secure, and works across every customer interaction channel.
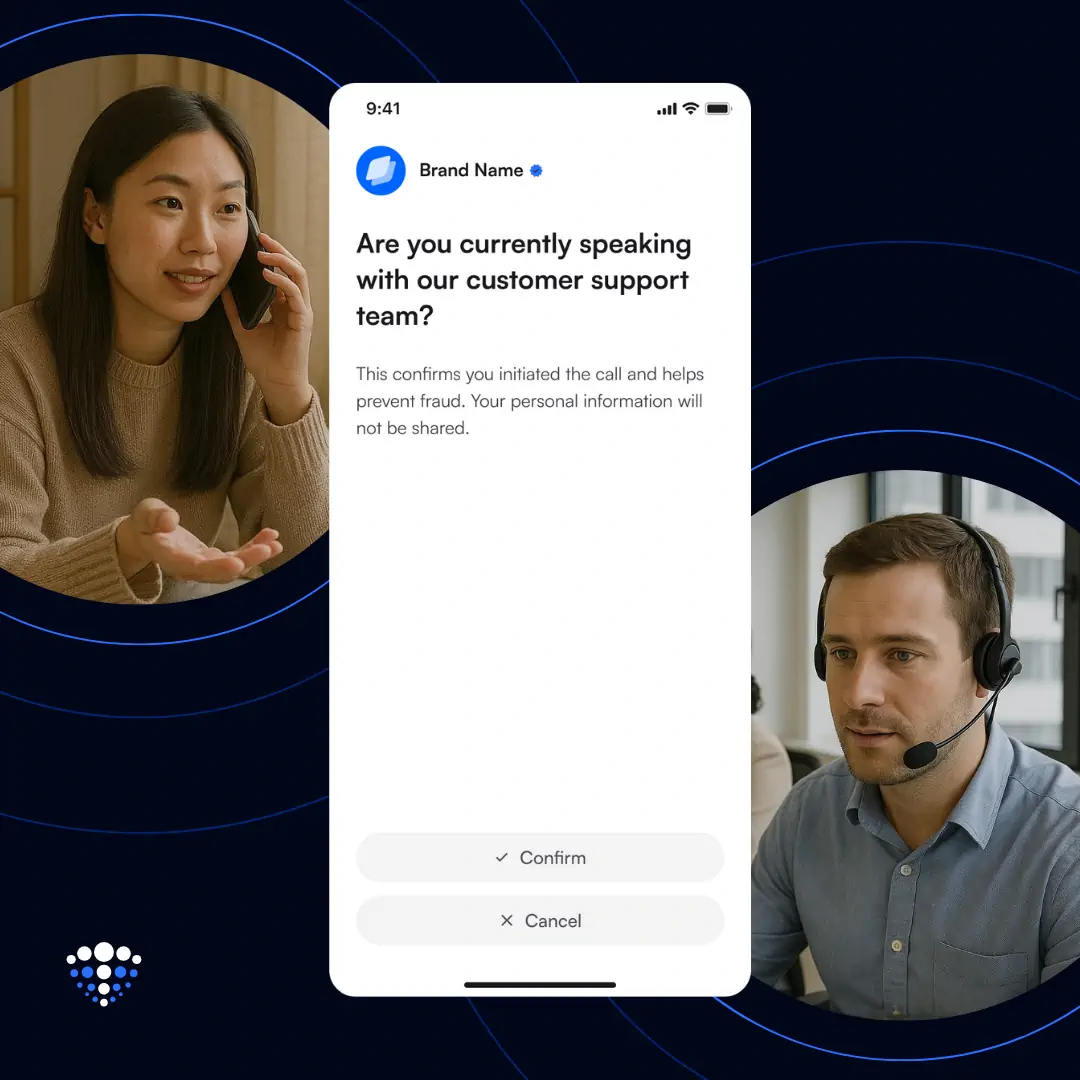
A strong alternative already exists. In a recent pilot with Telefónica, one of the world's largest telecom providers, users authenticated through a secure encrypted message sent directly to the organisation’s existing app. The user simply confirmed the request in the app, and the support agent instantly knew they were speaking with the right person. No OTPs, no shared secrets, and no sensitive information exposed.
This encrypted messaging protocol, called DIDComm, is a powerful replacement for SMS OTP on its own. It removes friction, prevents common fraud vectors, and works seamlessly in mobile or call centre environments.
In this blog, we break down why SMS OTP is no longer enough, how DIDComm offers a stronger alternative, and how digital ID credentials can enhance that alternative with verification capabilities that go far beyond a simple code.
Why Businesses Are Moving Away from SMS OTP
SMS OTP was introduced as a convenient second factor, but it has not kept pace with today’s security threats or user expectations. Companies across telecom, banking, retail, and public services are now reassessing OTP-based authentication and seeking alternatives that reduce friction while providing stronger protection.
Security vulnerabilities are getting harder to ignore
SMS OTP depends on a communication channel that was never designed for security. Attackers now routinely exploit weaknesses in mobile networks and user behavior:
- SIM swap fraud
- SMS interception
- Phishing and social engineering
- Malware that reads or forwards OTPs
- Account recovery flows vulnerable to hijacking
These weaknesses are well documented and widely exploited, making OTPs one of the easiest authentication factors to compromise.
Failure rates and user frustration keep rising
Users increasingly expect authentication to be fast, consistent, and device-agnostic. SMS OTP often delivers the opposite:
- Delayed or undelivered codes
- Switching between apps
- Users on poor networks unable to authenticate
- Higher drop-off rates during login or support interactions
In high-stress environments like call centres, even small delays significantly affect satisfaction and resolution time.
Global regulators are shifting away from OTPs
Countries and regulators are beginning to discourage or phase out SMS OTP for critical authentication, citing security and privacy risks.
In Europe, PSD3 is reinforcing the shift toward stronger, phishing-resistant authentication. While it does not explicitly ban SMS OTP, the direction is clear. Regulators are pushing financial institutions to adopt possession-based, cryptographic methods that minimise reliance on shared secrets and reduce vulnerabilities linked to OTP compromise. As EUDI wallets roll out, this shift is expected to accelerate.
Another clear example comes from the UAE becoming the first country to begin phasing out SMS and email OTPs for government services and moving toward more secure digital identity methods. This signals a broader trend: governments and enterprises are recognising that OTP-based authentication is no longer adequate for high-assurance identity verification.
Operational and financial costs are increasing
Supporting OTP flows is costly:
- Per-message carrier fees
- High support costs from failed OTP attempts
- Longer handle times in call centers
- Increased fraud losses linked to OTP compromise
As volumes scale, these costs become significant and persistent.
Businesses need an authentication method that is both secure and seamless
Organisations want stronger security, lower friction, and a better customer experience across channels. SMS OTP cannot deliver on all three. This is why enterprises are now looking to modern alternatives like DIDComm messaging and digital identity credentials, which provide cryptographic assurance without disrupting the user journey.
The Best Alternative to SMS OTP
The strongest replacement for SMS OTP is an authentication flow built on DIDComm’s encrypted messaging, with the option to enhance it using reusable digital ID credentials.
This creates two layers of value.
First, DIDComm on its own is a production-ready replacement for OTPs, already proven in a Telefónica contact centre pilot. Second, digital ID credentials can be added to extend the authentication flow with powerful identity verification capabilities that go far beyond a simple confirmation step.
Together, these two layers solve the security, friction, and operational challenges that OTPs can no longer address.
Alternative 1: DIDComm Encrypted Messaging (Already Proven in Telefónica’s Pilot)
DIDComm provides a secure, encrypted channel between the organisation and the user’s existing app. During authentication, the organisation sends a request directly to the user, who simply confirms it inside the app they already own. This bypasses SMS entirely and avoids all problems associated with code delivery, interception, or manipulation.
This is exactly the approach Telefónica tested in its recent pilot. Instead of waiting for an OTP, callers received a secure message in the app and confirmed it instantly. The support agent immediately knew they were speaking with the legitimate account holder, without asking for personal data or exposing sensitive information.
DIDComm on its own replaces OTPs with a faster and more secure flow. It removes friction, blocks SIM swap attacks and OTP interception, and works seamlessly across mobile, web, and call centre environments.
Alternative 2: DIDComm Plus Digital ID Credentials (Enhanced Capabilities Beyond Authentication)
Once DIDComm establishes a secure channel, organizations can build on it by issuing digital ID credentials to their users. These credentials can contain verified information from onboarding or previous ID verification checks and are stored in the user’s ID wallet (embedded in the company’s existing app).
During authentication, the organisation can request additional proofs through the same DIDComm channel. This enables verification of identity attributes, account ownership, or eligibility checks.
This turns a simple confirmation step into a powerful identity verification flow. The organisation no longer relies on shared secrets, and support agents do not need to ask for personal data. Users enjoy a streamlined, privacy-preserving experience based on reusable identity credentials.
DIDComm plus digital ID credentials gives businesses far more control than any OTP-based method. It delivers secure, repeatable, and privacy-first identity verification across all departments and channels.
Why These Two Layers Outperform Every Other SMS OTP Alternative
Most alternatives still rely on shared secrets or are limited to specific channels. Authenticator apps and SMS links improve the experience slightly but remain vulnerable to phishing or require fallbacks that recreate the same OTP weaknesses. Passkeys offer strong phishing resistance, but they were not built for call centre interactions, multi-device flows, or account recovery. Digital ID credentials solve all three while providing cryptographic proof of the user’s identity, not just the device (more on this later).
DIDComm provides a secure pipe for instant, cryptographic confirmation. Adding digital ID credentials expands this into a reusable identity verification system that works anywhere a business needs to confirm who a user is.
This combination delivers security, speed, and trust in ways SMS OTP will never be able to match.
Results From the Telefónica Contact Center Pilot
The strongest validation that DIDComm can replace SMS OTP comes from a recent pilot run by Telefónica, one of the world’s largest telecom providers. The goal was simple: reduce authentication time and eliminate the risks associated with SMS OTP and knowledge-based questions during customer support calls.
Instead of relying on OTPs, callers authenticated through a secure encrypted message delivered directly inside the organisation’s existing app. The user confirmed the request with a single tap, and the agent instantly received cryptographic proof that they were speaking with the correct account holder. No codes, no personal data exchanges, and no exposure of sensitive information.
DIDComm delivered faster and more secure authentication
The pilot demonstrated that DIDComm-only authentication can replace SMS OTP immediately and at scale. Key outcomes included:
- Authentication reduced from minutes to seconds
Callers were verified almost instantly. No waiting for codes, no repeated attempts, no frustration caused by network delays. - No sensitive data shared with agents
Agents did not need to ask for names, dates of birth, or account information. This removed a major social engineering risk and improved caller privacy. - Strong protection against SIM swap and OTP interception
Because no OTP was sent and no secrets were shared, attackers had nothing to intercept or manipulate. - Reduced operational strain in the call centre
Faster authentication freed up agent time, lowered handle times, and improved the experience for customers and staff.

A foundation for enhanced digital identity
Most importantly, Telefónica’s pilot shows that DIDComm-only authentication works today. Organisations can deploy this immediately as a superior replacement for SMS OTP. And once the secure messaging layer is in place, it becomes straightforward to extend the flow with digital ID credentials to further strengthen identity verification.
The result is an authentication model that is faster, safer, and more resilient than anything based on OTP codes.
How DIDComm and Digital ID Authentication Compares to Other SMS OTP Alternatives
Many organizations exploring replacements for SMS OTP gravitate toward options like authenticator apps or passkeys. While each improves certain aspects of the user experience, none address the full set of challenges around security, cross-channel authentication, account recovery, and identity verification.
DIDComm messaging and digital ID credentials, used together or independently, solve these gaps by eliminating shared secrets and enabling cryptographic proof of identity across every customer interaction channel.
Below is how they compare.
Authenticator Apps
Pros:
- Familiar to users
- Easy to deploy
- Slightly more secure than SMS OTP
Limitations:
- Still rely on shared secrets
- Vulnerable to phishing and social engineering
- Users often lose access when changing devices
- Still require fallback authentication methods that recreate the same OTP problems
- Authenticator apps generate one-time codes but cannot support contextual or multi-option challenges. They always produce a single numeric code.
DIDComm and Digital ID advantage:
- No shared secrets
- Resistant to phishing and interception
- Device changes do not break authentication when paired with recoverable credentials
- DID-based methods can request specific confirmations (e.g multiple choice), and digital ID credentials can add identity-attribute verification on top.
Email OTPs and Magic Links
Pros:
- Easy to implement
Limitations:
- Often considered weaker than SMS OTP for high-risk flows
- High interception risk
- Slower and more error-prone
- Not compliant with high-assurance identity requirements
DIDComm and Digital ID advantage:
- Cryptographically verifiable
- Not dependent on email delivery infrastructure
- Suitable for high-security scenarios
Passkeys
Pros:
- Strong phishing resistance
- Great for login on personal devices
Limitations:
- Not designed for call centre customer authentication
- Only verifies the device, not the user’s identity
- Limited use in multi-device or shared-device scenarios
- Passkeys can complicate account recovery when users lose access to all their trusted devices.
- Tied to hardware and platform ecosystems rather than identity portability
- Passkeys provide only binary authentication (yes or no) and cannot support contextual or multi-option challenges.
DIDComm and Digital ID advantage:
- Works across channels including call centres
- Not tied to a specific device or manufacturer
- Digital ID credentials provide reusable identity across devices, platforms, and services
- DIDComm can request more granular confirmations (e.g multiple choice), and digital ID credentials further expand this by enabling verification of specific identity attributes.
- Ideal for account recovery and delegated scenarios where passkeys fall short
Biometric Authentication
Pros:
- Good UX
- Strong device-level security
Limitations:
- Only verifies the device, not the user’s identity
- Not suitable for remote account recovery
- Cannot prove attributes or prior verification
DIDComm and Digital ID advantage:
- Biometrics can unlock the user’s digital credentials, combining strong authentication with verifiable identity
- Enables selective disclosure and zero-knowledge proofs
- Suitable for sectors requiring attribute-level verification
Where DIDComm and Digital ID Stand Out
Most OTP alternatives improve one dimension of the user experience but still rely on the weakest part of authentication: shared secrets and assumptions about device ownership.
DIDComm removes these weaknesses entirely by creating a secure, encrypted communication channel for instant, cryptographically reliable confirmation. Adding digital verifiable credentials expands this into a reusable identity system where users can prove exactly who they are across any channel, including high-pressure environments like call centres.
This combination outperforms every other OTP replacement because it solves the entire problem, not just the symptoms.
Real Business Impact: Replacing SMS OTP
Replacing SMS OTP is not only a security upgrade. It has a measurable impact on customer experience, operational efficiency, fraud reduction, and support-team performance. DIDComm authentication, with the option to enhance it using digital ID credentials, delivers clear improvements across every area where OTPs create friction or risk.
Below are the most significant results organizations see when they move away from OTP-based authentication.
Faster Authentication and Lower Drop-Off Rates
SMS OTP delays are one of the most common causes of abandoned logins and stalled support interactions. DIDComm removes these delays entirely by sending a secure, instantly delivered request to the user’s existing app.
Impact:
- Authentication drops from minutes to seconds
- Fewer failed attempts
- Higher completion rates on login, checkout, and support flows
- Improved handle times in call centres
Reduced Fraud and Stronger Identity Assurance
SMS OTP is easy to intercept, forward, or socially engineer. SIM swap fraud remains a major attack vector across telecom, banking, and fintech.
DIDComm eliminates the entire OTP attack surface by removing codes from the flow. Adding digital ID credentials provides cryptographic proof of identity and allows attribute-based verification, further reducing impersonation and account takeover.
Impact:
- No OTPs to intercept or phish
- Strong resistance to SIM swap and device compromise
- Clear proof of user identity, not just device possession
- Lower fraud losses and fewer recovery cases
Shorter Call-Centre Handle Times
Authentication is often the most time-consuming part of a support call. Agents must ask multiple security questions, confirm personal data, or wait for users to receive OTPs.
With DIDComm, callers verify themselves in seconds, and agents instantly see a trusted confirmation. Digital ID credentials can eliminate the need to ask for names, dates of birth, or account-related information.
Impact:
- Handle times drop significantly
- Agents spend more time solving the actual issue
- Lower operational costs
- Reduced stress for customers and support staff
Better Customer Experience Across Every Channel
Users want authentication that is fast, consistent, and secure. DIDComm provides the same simple confirmation flow across mobile, web, and call centres. Adding digital ID credentials allows users to prove verified information without exposing personal data.
Impact:
- A consistent experience regardless of channel
- No switching apps or waiting for codes
- Privacy-preserving interactions
- Higher satisfaction and retention
Lower Operational and Infrastructure Costs
OTP flows are expensive to operate. Organisations pay for SMS delivery, handle failed authentication attempts, manage fraud incidents, and maintain fallback verification processes.
DIDComm removes all SMS costs and reduces the workload associated with OTP failures. Digital ID credentials decrease manual reviews, repeat verifications, and recovery processes that contribute to operational overhead.
Impact:
- Elimination of SMS fees
- Fewer manual checks
- Lower fraud and support costs
- A more efficient authentication stack
Future-Proofing Your Identity Strategy
OTP-based authentication is already being phased out in some markets, and regulatory guidance in Europe and globally is shifting toward phishing-resistant, cryptographic methods. DIDComm provides the secure messaging layer required for modern authentication, while digital ID credentials create a reusable identity foundation that supports new use cases as they emerge.
Impact:
- Compliance with evolving security expectations
- Compatibility with digital ID wallets and verifiable credential ecosystems
- Flexibility to expand into higher-assurance use cases
- A long-term alternative that adapts as standards evolve
How Truvera Helps You Implement a Modern SMS OTP Alternative
Truvera gives organizations everything they need to replace SMS OTP with secure, frictionless authentication based on DIDComm and digital ID credentials. It provides the end-to-end infrastructure for issuing credentials, sending encrypted authentication requests, verifying cryptographic proofs, and integrating this into existing apps and support workflows.
Whether you want a direct replacement for SMS OTP (DIDComm-only) or you want to enhance authentication with reusable digital identity credentials, Truvera makes implementation fast, scalable, and compliant.
Instant DIDComm Authentication Through Your Existing App
Truvera allows you to replace SMS OTP by sending users a secure authentication request directly inside your existing mobile app. Users simply confirm the request with a tap, and Truvera delivers a cryptographically verifiable response back to your systems.
Key benefits:
- No SMS codes
- Instant delivery and confirmation
- No shared secrets or OTP vulnerabilities
- Seamless user experience inside your current app
This is the same method Telefónica used in their pilot, where callers were verified in seconds without sharing any personal information with agents.

Add Digital ID Credentials for Stronger Identity Verification
If you want to go beyond basic authentication, Truvera lets you issue reusable digital ID credentials to your users. These credentials can contain verified identity data from onboarding, ID verification checks, or any internal verification process.
Through the DIDComm channel, Truvera enables you to request additional proofs during authentication, such as:
- Identity attributes (name, date of birth, address)
- Proof of account ownership
- Confirmation of a previous IDV check
- Age or eligibility checks
- All of the above can support Zero-knowledge proofs to verify the attributes without revealing the data that supports those proofs
This allows organizations to authenticate the user and verify who they are, not just which device they hold.
Flexible Deployment: REST API, Mobile SDK, and Cloud Wallet
Truvera is designed to drop into your existing architecture with minimal effort.
You can integrate Truvera using:
- A REST API for sending DIDComm authentication requests and receiving the responses
- A mobile SDK to add wallet functionality to your existing app and the ability to decrypt and respond to DICComm messages
- A cloud wallet option for users who do not want or need a mobile app
This gives you multiple implementation paths depending on your product strategy and timelines.
Stronger Call Centre Authentication Without Agent Risk
Truvera enables call centre agents to verify callers without asking for personal data. Agents send an authentication request from their CRM or support tool, and the caller confirms it in the app. The agent receives a verified response instantly.
No sensitive data exposed. No security questions. No OTP failures.
Built for High-Assurance Use Cases
Truvera uses verifiable credentials based on W3C standards and encrypted DIDComm messaging, ensuring strong cryptographic guarantees across all interactions.
This gives organizations a compliant, future-proof alternative to OTPs that aligns with emerging digital identity standards.
Implementation Guide: How Companies Replace SMS OTP With DIDComm and Digital ID
Replacing SMS OTP does not require rebuilding your authentication system. Companies typically roll out DIDComm authentication in a few weeks, starting with one user journey and expanding gradually. Here is how the process works in practice.
Step 1: Choose the First Journey to Upgrade
Most organizations start by replacing OTPs in the areas where they create the most friction, such as:
- Login and account access
- High-risk actions (password changes, transactions)
- Call centre identity verification
- Account recovery
- Fraud-prone flows
This allows teams to validate the new experience quickly.
Step 2: Enable Users to Receive DIDComm Messages
For DIDComm authentication to work, users need a wallet or app capable of receiving secure messages.
You can choose between:
- Integrating Truvera’s mobile SDK into your existing app
This adds DID-based secure messaging directly into your product. - Using Truvera’s cloud wallet
Ideal when your organization does not have a mobile app.
Step 3: Replace SMS OTP With a DIDComm Confirmation Request
Instead of sending a one-time password by SMS, your system sends a secure authentication request to the user’s app through Truvera’s messaging layer.
The user receives a notification, opens the app, and approves the request with a simple tap. This approval cannot be intercepted or manipulated.
You receive the confirmation instantly and can proceed with login, transaction approval, or caller verification, without any codes.
Step 4: Add Digital ID Credentials for Stronger Verification (Optional)
Once the secure messaging channel is in place, organizations can issue digital ID credentials to the users’ wallets. These credentials can represent:
- Identity attributes
- Completed ID verification checks
- Account ownership
- Age or eligibility
- Customer entitlements
During authentication, you can request these proofs over the same DIDComm channel.
The user approves the request, and Truvera verifies the credential.
This adds identity assurance on top of the simple confirmation flow.
Step 5: Connect Authentication Results to Your Existing Systems
Using Truvera’s REST API, authentication confirmations or credential verifications can be sent to your existing:
- Support tools
- Call centre systems
- IAM or CIAM
- Fraud engines
- Internal dashboards
This allows DIDComm to replace SMS OTP without changing downstream workflows.
Step 6: Test and Roll Out Gradually
Most companies follow a simple rollout path:
- Pilot internally
- Enable DIDComm for a limited user group
- Compare performance with OTP in parallel
- Expand as adoption grows
- Fully deprecate OTP once confidence is high
Because users only need to tap “Approve,” adoption rates tend to be very strong.
Step 7: Monitor Results
Organisations typically track:
- Authentication speed
- Success and completion rates
- Call centre handle time
- Fraud attempts
- Reduction in OTP-related support tickets
- User satisfaction
This data helps identify additional flows where OTPs can be removed.
What This Enables
By following these steps, companies implement an authentication method that is:
- Faster
- More secure
- Phishing-resistant
- Easier for users
- More private
- Ready for future digital identity ecosystems
DIDComm replaces the OTP channel. Digital ID credentials add reusable identity verification.
Together, they create a modern authentication experience that works across every customer interaction channel.
Conclusion
SMS OTP served its purpose for many years, but it can no longer keep up with modern security threats or user expectations. It slows people down, exposes businesses to avoidable fraud, and creates unnecessary friction in high-pressure moments like login, account recovery, and customer support calls.
DIDComm authentication offers a stronger and more intuitive alternative by replacing OTP codes with secure, encrypted confirmation requests sent directly to a company’s existing app. It removes delivery failures, blocks common attack vectors, and dramatically improves the customer experience. When combined with digital ID credentials, it becomes a powerful identity verification layer that works across any channel and supports high-assurance use cases.
The results seen in the Telefónica pilot make it clear that this approach works in real environments with real users. It is faster, safer, and much easier to operate than anything based on OTPs.
As more organizations move toward phishing-resistant, cryptographic authentication, DIDComm and digital ID credentials are becoming the natural evolution of how businesses verify their users. Companies that modernize now will not only reduce fraud and operational costs, but also deliver a smoother and more trusted experience across every customer interaction.
If you are ready to move beyond OTPs, the shift is simpler than you think, and the impact is immediate.
Frequently Asked Questions About SMS OTP Alternatives
What are the main alternatives to SMS OTP?
Common alternatives include authenticator apps, push notifications, passkeys, email links, and digital identity–based authentication. Each option improves certain aspects of security or user experience, but they vary widely in reliability, phishing resistance, and suitability for multi-channel environments such as call centres.
Why are companies moving away from SMS OTP?
SMS OTP creates friction for users, and is vulnerable to SIM swap attacks, phishing, and message interception. Organisations also face rising SMS costs and increasing regulatory pressure to adopt phishing-resistant authentication.
What is the strongest alternative to SMS OTP today?
The strongest alternatives use cryptographic authentication instead of shared secrets or one-time codes. This includes DIDcomm-based approaches where users confirm requests inside a company’s existing app or wallet and where responses are verified using digital signatures rather than SMS infrastructure.
Can digital ID credentials replace SMS OTP?
Yes. Digital ID credentials allow users to authenticate and prove identity attributes through cryptographically signed presentations. This removes the need for SMS codes and provides much stronger identity assurance, making it well-suited for login, account recovery, support calls, and regulated workflows.
Why are SMS OTP alternatives important for call centres?
Call centres rely heavily on identity verification, and SMS OTP introduces long wait times, high failure rates, and opportunities for social engineering. Alternatives that allow users to confirm their identity inside a company’s existing app or wallet reduce handle time, improve security, and eliminate the need for agents to collect personal data.
Are SMS OTP alternatives user-friendly?
In most cases, yes. Modern authentication methods allow users to tap to approve requests, use biometrics for confirmation, or present a stored digital ID credential. These experiences are faster and more reliable than waiting for codes.
How do I choose the right SMS OTP alternative?
The best choice depends on your channels and security needs. For web logins, passkeys may be sufficient. For mobile users, in-app confirmations can deliver a better experience. For multi-channel environments or high-assurance identity verification, digital ID credentials or cryptographically signed confirmations provide the strongest alternative.






