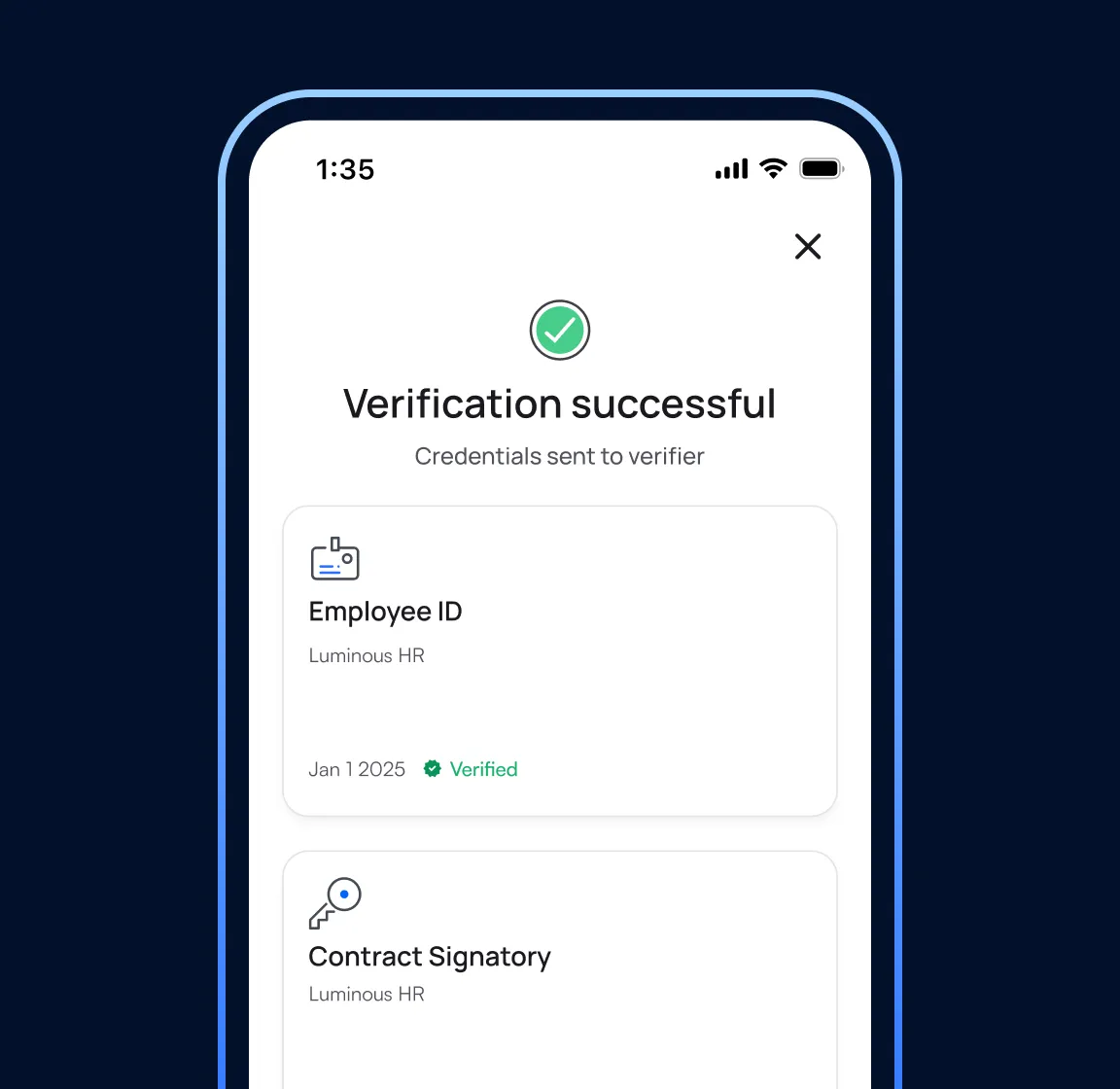
Verify Identity and Authority
Protect against fraud and impersonation
Credentials are tamper-proof, cryptographically signed by the issuing company, and easily auditable, so you know they haven’t been faked or forged.
Instantly verify who someone represents
Avoid delays and confusion by giving partners, clients, or regulators cryptographic proof of a person’s authority.
Enable secure, role-based access
Use verifiable credentials to control who can do what in internal and external systems, without creating new accounts or passwords.
Keep everything up to date
When someone’s role changes, so can their credentials. No more relying on outdated spreadsheets or approvals.
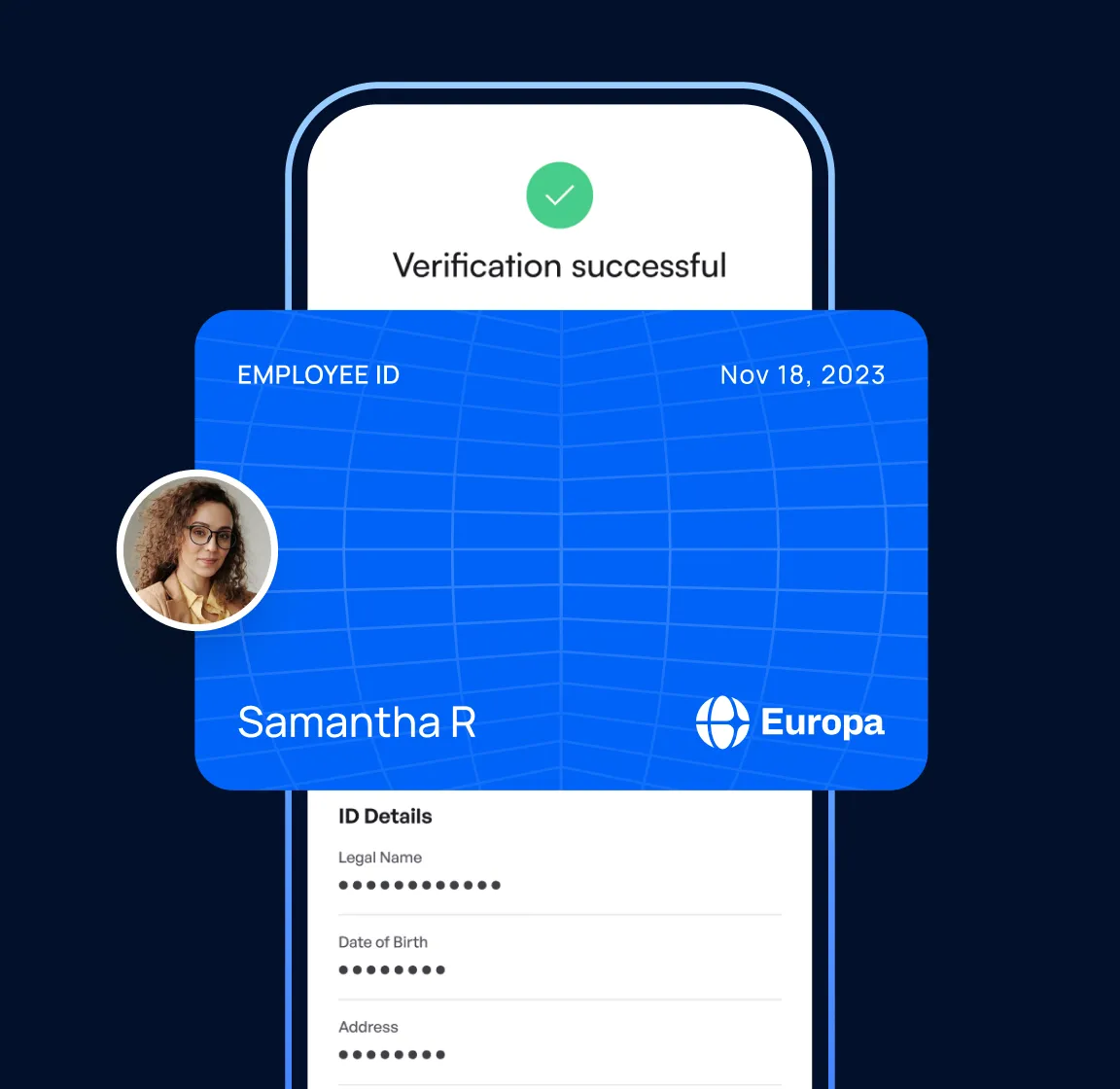
Make Roles and Permissions Verifiable
From legal contracts to regulated filings, delegated authority credentials can streamline workflows in:
Financial Services
Empower employees or third parties to act on behalf of a business client with a verifiable mandate.
Government & Public Sector
Accept digital representations of power-of-attorney, without the paperwork.
Logistics & Supply Chain
Ensure a delivery driver or freight forwarder is actually authorized by the sender, before handing over sensitive and costly goods.
Professional Services
Let accountants, legal representatives, or consultants prove they’re authorized to act on behalf of their clients.
Enterprise IT
Simplify identity federation across partners with cryptographically verifiable roles and access scopes.
Ready to Issue or Accept Delegation Credentials?
Whether you’re a government agency, enterprise, or digital service provider, we can help you:
Issue delegated authority credentials that confirm a person’s name, role, organization, and what they’re authorized to do.
Bind a biometric to a credential, ensuring that only the intended individual can use their authority credential.
Audit and remotely revoke credentials, keeping authority in sync with changing roles or contracts.

Create your first digital ID credential today
The Truvera platform helps you integrate reusable ID credentials into your existing identity workflows to support a variety of goals: reduce onboarding friction, connect siloed data, verify trusted organizations and customers, and monetize credential verification.