Call centers today face a difficult balancing act: verify callers quickly, block fraud attempts, and maintain a frictionless customer experience. But with rising threats like phishing, SIM swap attacks, and deepfakes, traditional authentication methods like passwords, OTPs, and security questions are no longer enough.
That’s why many organizations are rethinking how they authenticate callers, moving toward faster, more secure, and privacy-preserving solutions.
In this article, we’ll break down the leading call center authentication solutions used today, from voice biometrics and multi-factor authentication to emerging models like digital ID wallets powered by verifiable credentials. You’ll learn how each method works, where it performs best, and which one is most future-ready.


Why Traditional Caller Authentication Falls Short
Most call centers still rely on methods like security questions and one-time passwords (OTPs) to verify who’s on the line. While these techniques may have worked in the past, they’re no longer effective against today’s threat landscape or today’s customer expectations.
Fraudsters now use tactics like SIM swap attacks, Caller Line Identification (CLI) spoofing, and phishing to bypass traditional checks. At the same time, data breaches have made knowledge-based authentication (KBA) nearly useless, since answers to “secret” questions are often publicly available.
On the business side, these outdated processes drive up Average Handle Time (AHT), frustrate customers, and put agents in the uncomfortable position of managing sensitive personal data. Worse, inconsistent or overly complex authentication flows can cause service delays and increase dropout rates.
That’s why many organizations are now evaluating modern call center authentication solutions that improve both security and customer experience.
Call Center Authentication Solutions Deep-Dive
Knowledge-Based Authentication (KBA)
How It Works:
Knowledge-Based Authentication (KBA) verifies a caller’s identity by asking them to answer pre-set questions. These might include personal details like date of birth, mailing address, recent transactions, or answers to “secret questions” chosen at account setup. KBA is typically conducted manually by the agent or automatically through IVR before routing.
Strengths:
- Simple to implement: No technical integration required.
- Familiar to users and agents: Longstanding process in financial services and government.
- Device-agnostic: Doesn’t depend on smartphone or app usage.
Weaknesses:
- Insecure: Answers can often be found or guessed using leaked data from breaches or public records.
- Time-consuming: Each question adds seconds or minutes to call duration.
- Poor user experience: Particularly frustrating when the customer is already authenticated on another channel.
- Compliance risk: Agents are exposed to personal data that must be stored, secured, and audited.
Infrastructure Requirements:
- Minimal technical setup.
- Scripts must be maintained and updated in the IVR or CRM system.
- Agent training required for proper execution and compliance handling.
Risk Level:
High: Easily bypassed by social engineering or stolen data, and creates privacy exposure for agents.
One-Time Passwords (OTPs) & Multi-Factor Authentication (MFA)
How It Works:
This category includes both traditional OTPs (one-time passwords) and broader forms of multi-factor authentication (MFA). In call center flows, an OTP is sent to the caller via SMS or email. The caller then reads the code to the agent or enters it through the IVR.
More advanced MFA adds a second factor (such as a hardware token, app approval, or biometric check) on top of a password or known detail.
Strengths:
- Widely adopted: Many customers are already familiar with OTP-based verification.
- Better than KBA: Adds an extra hurdle for attackers compared to static questions.
- Flexible delivery: Can be used via SMS, email, apps, or hardware tokens
Weaknesses:
- Vulnerable to SIM swap and phishing: Attackers can intercept OTPs or trick users into disclosing them.
- Still relies on shared secrets: The OTP must be communicated (often verbally) to the agent.
- No cryptographic binding: Verifies possession of a device or account, not the identity of the caller.
Many organisations are now actively searching for an sms otp alternative that avoids these weaknesses.
Infrastructure Requirements:
- Integration with OTP/MFA providers (e.g., Twilio, Authy, Duo, RSA).
- Secure handling of code entry or agent-side confirmation.
- Customer enrollment and fallback flows (e.g., “what if they didn’t receive the code?”).
Risk Level:
Moderate: Safer than KBA, but increasingly vulnerable to modern attack vectors like phishing kits and SIM swaps.
Voice Biometrics
How It Works:
Voice biometrics verify a caller’s identity by analyzing unique features in their voice, such as pitch, tone, cadence, and frequency patterns. Some systems require the caller to speak a specific phrase (active voice biometrics), while others analyze speech passively during a conversation (passive voice biometrics). The voiceprint is matched against a stored profile to authenticate the individual.
Strengths:
- Frictionless experience: Passive authentication can happen without interrupting the conversation.
- Device-independent: No smartphone or app required.
Weaknesses:
- Vulnerable to spoofing and deepfakes: Fraudsters increasingly use AI-generated voice clones.
- Environmental sensitivity: Accuracy drops in noisy environments or with poor call quality.
- Enrollment required: Customers must create a reliable voiceprint in advance.
- High false reject/accept rates: Especially for people with colds, accents, or speech impairments.
Infrastructure Requirements:
- Requires voice biometric engine (on-prem or cloud).
- Integration with IVR or agent desktop.
- Secure storage and management of biometric templates.
- Monitoring tools to detect spoofing or replay attacks.
Risk Level:
Moderate: Passive and low-friction, but increasingly at risk due to voice cloning and technical variability.
Digital ID Wallets & Verifiable Credentials
How It Works:
Digital ID wallets enable users to store and present verifiable credentials, digital proofs of identity issued by a trusted organization (like a bank or telecom provider).
In the contact center flow, when a customer calls in, the agent clicks “Authenticate Caller,” and the system sends a push notification to the customer’s mobile app (where the wallet is embedded). The user confirms the request using a biometric unlock (e.g. Face ID), and the call is instantly verified, without exposing any personal data.
This technology was successfully tested in a pilot by GSMA, Telefónica Tech, and Dock Labs, which proved that organizations can verify callers instantly and privately, without relying on passwords, OTPs, or voiceprints.
Strengths:
- Instant, cryptographic trust: Verifiable credentials confirm identity securely.
- Biometric, app-based approval: User confirms the call with Face ID or fingerprint.
- Privacy-preserving: No PII spoken, stored, or seen by the agent.
- Resistant to call center fraud: Eliminates risk from phishing, SIM swap, and deepfake attacks.
- Faster handle time: Cuts verification time by up to 80%
- Smooth UX: Seamless experience through the organization’s existing app. No need to download an extra app.
Weaknesses:
- Requires that the customer has the company’s mobile app (e.g. bank or telco) installed.
- May need user education or onboarding support in early rollout.
Infrastructure Requirements:
- Lightweight REST API integration for call center software.
- Mobile SDK to embed the wallet in the organization’s app.
- No backend data storage or biometric database required.
Risk Level:
Low: Cryptographically secure, resistant to modern attack methods, and compliant by design
What to Avoid When Choosing a Call Center Authentication Solution
Choosing the right call center authentication method isn’t just about what works, it’s also about what to avoid. Some solutions may appear secure on the surface but introduce hidden risks, compliance concerns, or unnecessary friction. Here are common pitfalls to steer clear of:
Overreliance on Static Data
Methods like knowledge-based authentication (KBA) and OTPs depend on information that can easily be stolen or guessed. If a solution relies solely on birth dates, addresses, or codes sent via SMS, it’s vulnerable to phishing, SIM swaps, and data breaches.
Ignoring the Privacy Surface Area
If your agents are hearing or handling personal data, you’re exposing the business to infringements to privacy regulations and internal security risks. Modern approaches should verify identity without putting PII in front of the agent.
Trusting Device Possession as Proof of Identity
Approaches like OTP-based MFA confirm access to a device, not who’s holding it. This leaves room for fraud when devices are lost, stolen, or compromised.
Overcomplicating Your Stack
Stacking multiple fragile or legacy solutions can increase support overhead and user frustration. Look for tools that integrate cleanly, scale easily, and reduce handle time, without requiring wholesale infrastructure changes.
Why Digital ID Wallets Are Emerging as the Preferred Call Center Authentication Solution Choice
As fraud tactics evolve and customer expectations rise, organizations are turning to digital ID wallets powered by verifiable credentials as the most future-proof authentication solution for call centers.
Unlike methods that rely on security questions or SMS codes, digital ID wallets offer cryptographic assurance that the caller is who they claim to be, without requiring them to share personal information or complete multi-step flows.
This model allows organizations to:
- Authenticate callers instantly using biometric approval inside their existing mobile app (e.g. the bank or telecom provider’s app).
- Protect customer privacy by keeping sensitive data out of the call.
- Prevent fraud by blocking phishing, SIM swap, and spoofing attacks.
- Reduce handle time by eliminating security questions and manual verification steps.
- Stay compliant with data protection regulations.
This approach was tested in a real-world pilot by GSMA, Telefónica Tech, TMT ID and Dock Labs, which showed that customers could confirm their identity with a single tap, and agents received a verified status without ever hearing personal details.
For organizations with an existing customer app (e.g. telcos, banks, insurers), adding a verifiable credential wallet is a fast, lightweight upgrade that delivers measurable gains in security, efficiency, and customer experience.
Truvera’s Call Center Authentication Solution at a Glance
Truvera offers a modern, privacy-first authentication solution designed specifically for contact centers. Built on verifiable credential technology, it allows your organization to verify callers instantly, without relying on security questions, OTPs, or data exposure.
Here’s how it works:
- The agent clicks “Authenticate Caller.” on their portal.
- The customer receives a push notification in your existing mobile app.
- The customer opens the app using biometrics (e.g. Face ID) and confirms that they are speaking with the support team.
- The agent sees a Verified status in real time, without accessing any personal data.
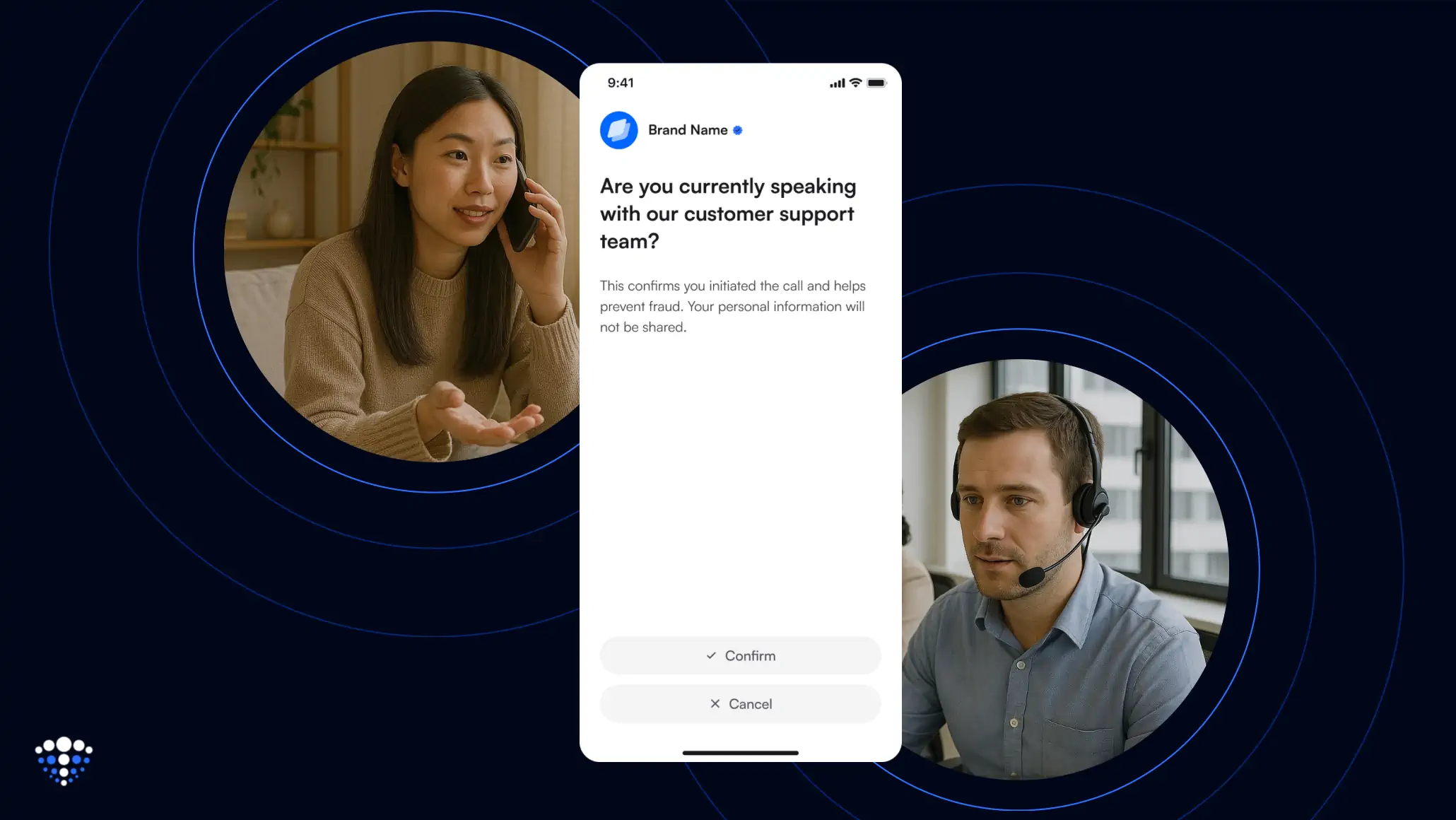
What sets Truvera apart:
- Secure by design: Resistant to phishing, SIM swap, and spoofing.
- Privacy-preserving: No PII exchanged between caller and agent.
- Fast integration: Lightweight REST API and mobile SDK
- Tested and proven: Validated in the GSMA and Telefónica pilot.
- Built for scale: Supports telecom, banking, government, and more.
If your organization has a mobile app, Truvera can turn it into a secure digital ID channel, reducing handle time, lowering fraud risk, and delivering a seamless authentication experience.
Key Takeaways
- Call center authentication best practices are no longer just about verifying identity, it’s about doing it fast, securely, and without exposing sensitive data.
- Legacy methods like KBA, OTPs, and even voice biometrics have major drawbacks: they’re slow, vulnerable to fraud, and often intrusive.
- Digital ID wallets using verifiable credentials offer the strongest combination of speed, security, and privacy, verifying identity instantly through your organization’s app.
- Truvera’s call center authentication solution, tested by GSMA and Telefónica, gives agents real-time confirmation with no PII exposure, lowering handle time and fraud risk in one step.
FAQ: Call Center Authentication Solutions
1. What is the most secure authentication method for call centers?
Digital ID wallets using verifiable credentials are among the most secure options for a call center to authenticate customers. They use cryptographic proof, biometric verification, and encrypted communication to confirm the caller’s identity, without exposing sensitive data or relying on vulnerable factors like OTPs or security questions.
2. Is voice biometrics safe for caller authentication?
Voice biometrics can improve experience, but they are increasingly vulnerable to deepfake audio and background noise. While useful in some scenarios, they’re not sufficient for high-assurance authentication on their own.
3. What are the drawbacks of OTP-based verification?
OTPs sent by SMS or email are vulnerable to phishing, SIM swap attacks, and delivery issues. They confirm device possession, not identity, and often add friction to the call flow.
4. How do verifiable credentials work in a call center?
When a caller contacts support, the agent triggers a push notification via the organization’s app. The customer opens the app with biometrics, and confirms that they are speaking with support. The agent sees a verified result in real time, no personal questions or PII exchange required.
5. Can this work with our existing call center and mobile app?
Yes. Truvera’s call center authentication solution integrates via a lightweight REST API and embeds directly into your existing mobile app. No new app is required, and most organizations can pilot in just a few weeks.






