How Decentralized ID works
Decentralized ID allows companies to generate tamper-proof digital credentials containing user information or identifiers. These credentials are stored by the user in a digital ID wallet and enable companies to pinpoint the exact person they’re verifying during onboarding, across multiple clients or siloed internal systems.

Core Components
Verifiable Credentials
Verifiable credentials are digital, cryptographically secured representations of identity information that cannot be modified or corrupted. These credentials are issued by trusted organizations, such as ID companies, governments, financial institutions, or businesses. They ensure authenticity and integrity of the information contained in them, allowing organizations to verify the user’s identity with confidence, without the risk of tampering or fraud.
Digital ID Wallets
Digital ID wallets store and manage verifiable credentials, providing users with control over their identity information. These wallets can be mobile app-based, allowing users to manage their credentials on the go, or cloud-based, offering flexibility depending on your organization’s needs. With digital ID wallets, users can present their credentials securely across different platforms and systems, streamlining the verification process while maintaining privacy and security.
How Decentralized ID Works
01 Issuance of a Verifiable Credential
When a user completes onboarding with one of your clients or siloed systems, you issue them a digital credential that identifies them. This credential is made tamper-proof using advanced cryptography to ensure security. The credential can include specific personal data, or simply an identifier that links them to your system—it’s entirely customizable to your needs.

02 Credential storage
The digital credential is securely stored by the user, either on your app, your client’s existing app, or in the cloud. This provides users with control over their credentials and ensures they have easy access when needed.

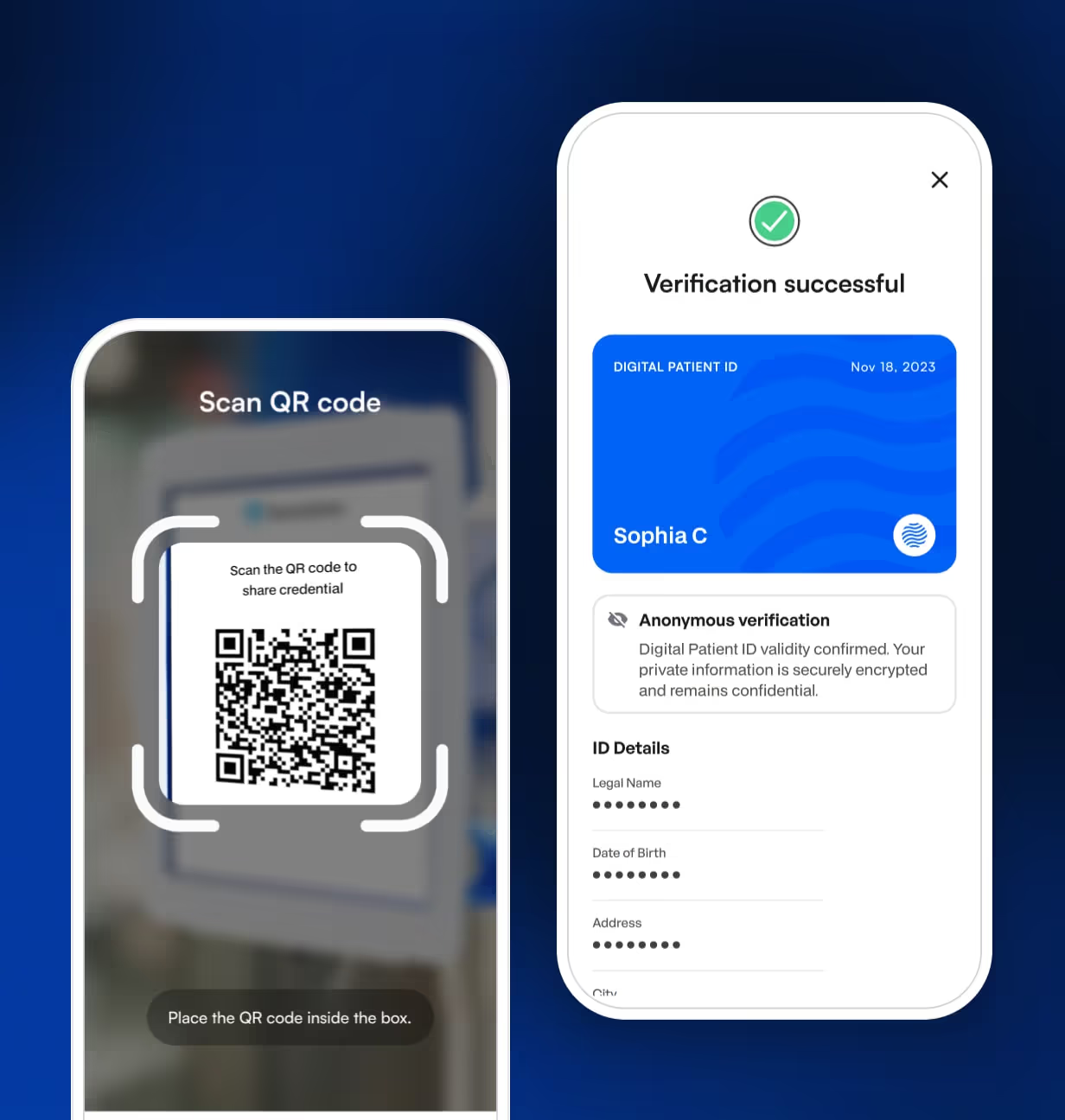
03 Onboarding and credential presentation
When the user later onboards with another one of your clients or siloed systems, they present the credential. During the onboarding process, the user will have the option to sign in using their verifiable credential by scanning a QR code to securely share it. This allows you to instantly recognize and match the user, speeding up the onboarding process.

04 Secure data exchange and privacy
The entire verification process is end-to-end encrypted, ensuring secure data exchange at every step. The user remains in full control of their data and must provide consent before any information is shared.

05 Continuous use across systems
Users can reuse their verifiable credentials across multiple platforms and systems, eliminating the need for repetitive data entry and document submissions. This ensures a seamless and frictionless experience each time.

Unlocking value across industries
Integrating Decentralized ID technology is not about displacing current offerings but enriching them. It easily integrates with existing services, leading to additional revenue streams without disrupting the established business model.
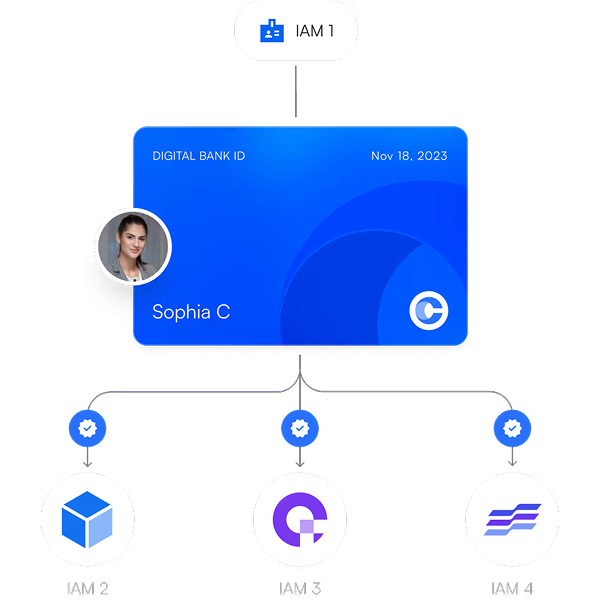
IAM: Connect Data Silos Across Systems
Enable user onboarding across multiple siloed IAM systems. Eliminate redundant onboarding without centralizing systems. Instantly recognize users across platforms for improved user experience and operational efficiency.
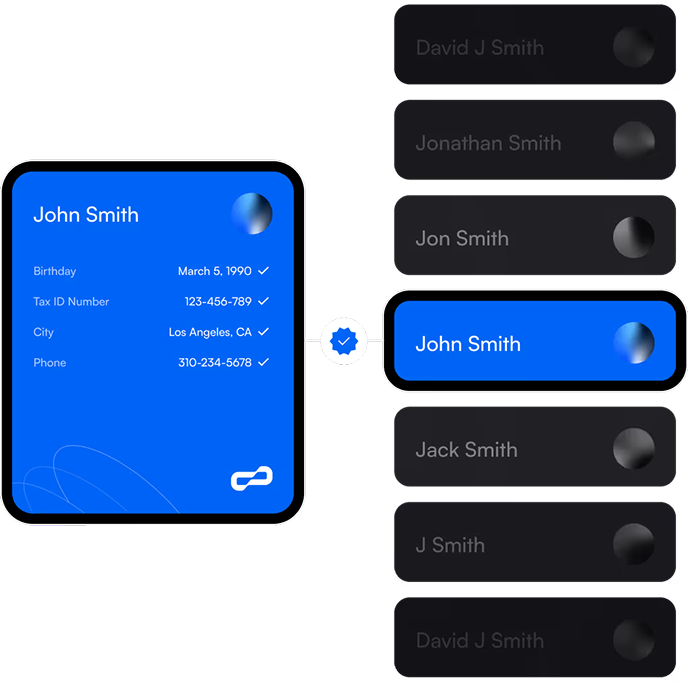
IDV Providers: Reduce Onboarding Friction
Quickly identify the exact person you're trying to verify across your clients. Enhanced customer data matching reduces onboarding friction, boosts conversion rates in your clients' acquisition funnels, and elevates your position in their KYC hierarchy.
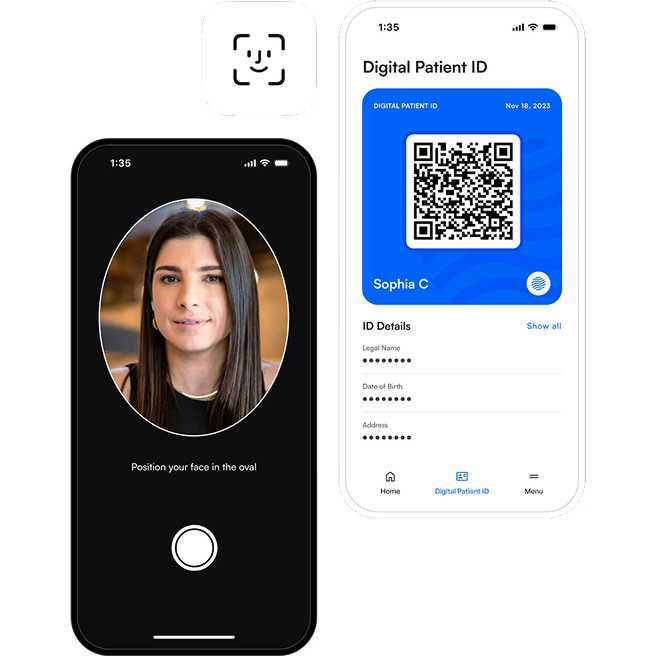
Bind Biometric Data to ID Credentials
Tying biometrics to verifiable credentials ensures the credential presenter is the original recipient. Verifiable credentials enable secure transfers without exposing sensitive biometric data, ensuring regulatory compliance.
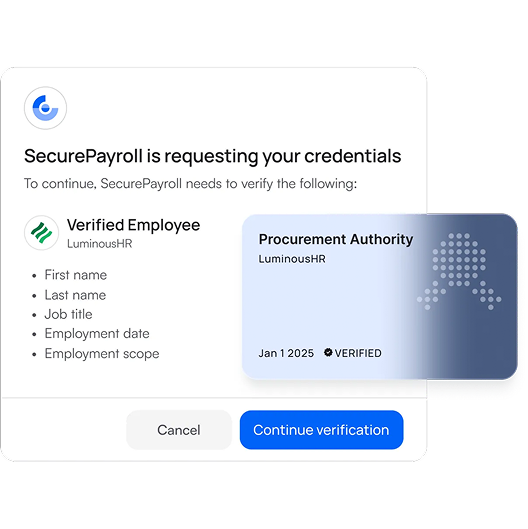
Delegatable Authority
Verifiable credentials make delegation of authority digital, instant, and secure. Issue tamper-proof credentials that prove a person’s role, permissions, and organizational affiliation so you can trust every action they take.
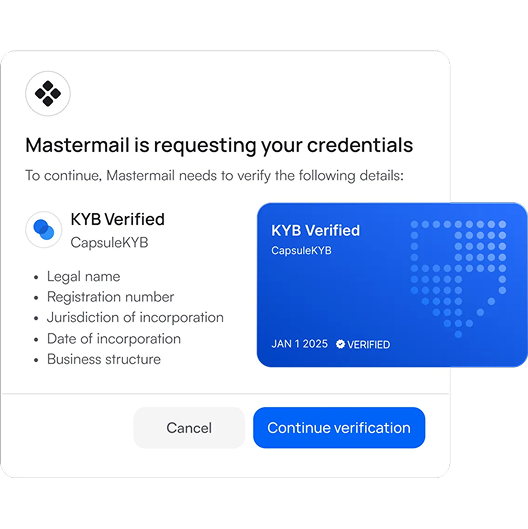
Reusable KYB
Know-Your-Business checks are essential but repetitive and costly. Each time a business applies for a service, they must resubmit registration papers, ownership structures, tax IDs, and licenses. Verifiable credentials change that.
Deploy 12x faster
Why build all the infrastructure yourself? With the Truvera API, you can integrate with your system and data sources to deploy your entire Decentralized ID solution up to 12 times faster than using open-source options.
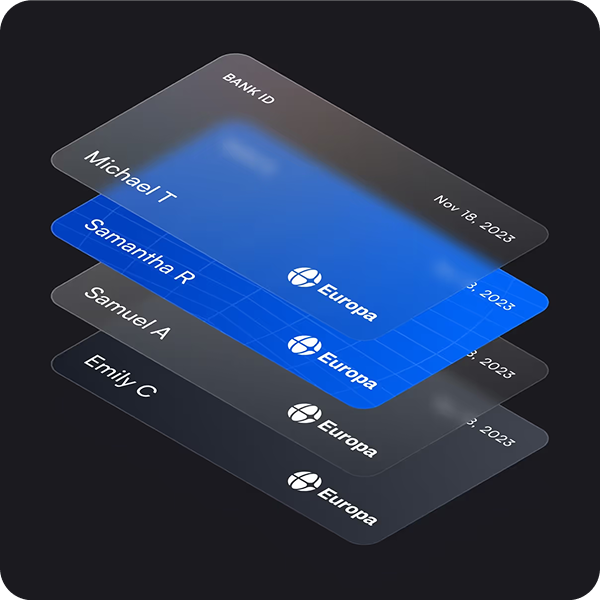
Faster customer data matching, without adding friction




Why choose Truvera?
Dock Labs is a leader in decentralized identity solutions, empowering businesses to launch ID ecosystems where their partners can create, share, and monetize verifiable digital credentials. The Truvera platform is designed to be easily implemented and scalable, allowing organizations to quickly deploy a decentralized identity solution with minimal development overhead.
REST API for core functions
Wallet SDK for wallet deployment
Developer-friendly integration
Create your first digital ID credential today
The Truvera platform helps you integrate reusable ID credentials into your existing identity workflows to support a variety of goals: reduce onboarding friction, connect siloed data, verify trusted organizations and customers, and monetize credential verification.






