Fraud-Proof Supply Chain Certificates
With Dock’s blockchain-based Certification Platform, you can issue fraud-proof digital documents that are instantly verifiable for authenticity — creating complete visibility of the entire supply chain for all stakeholders, reducing fraud, and providing transparent product data for customers.







The benefits of fraud-proof supply chain certificates
Save time and money with instant verification
Paper and PDF documents are very easy to fake, and verifying their authenticity is a slow, manual, and costly process. By integrating blockchain capabilities into your logistics software, you can rest assured that your digital documentation cannot be forged or counterfeited. You'll be able to issue and verify Supply Chain documentation confidently while creating an auditable trail from origin through consumption, ensuring authenticity at every stage of your product's journey.
Increase trust and transparency
Consumers increasingly seek companies that produce ethically and environmentally responsible products, but product certifications can be easily faked. By leveraging Dock’s blockchain technology to create fraud-proof documentation, you can provide transparency about a product's provenance and handling while ensuring that all the data is trustworthy and can be instantly verified for authenticity.
Easily integrate blockchain technology
In 2017, Walmart, Nestlé and other food giants announced they were using blockchain technology for food traceability. But blockchain has been complex and expensive to integrate, only available to industry giants. Until now. With Dock's simple API and a few lines of code, you can get all the benefits of blockchain technology without building it yourself, saving you time and money.
How it works

1. Connect
Dock’s Certification Platform integrates with your Logistics or Certification Software via a simple API, supercharging your existing system with blockchain capabilities.
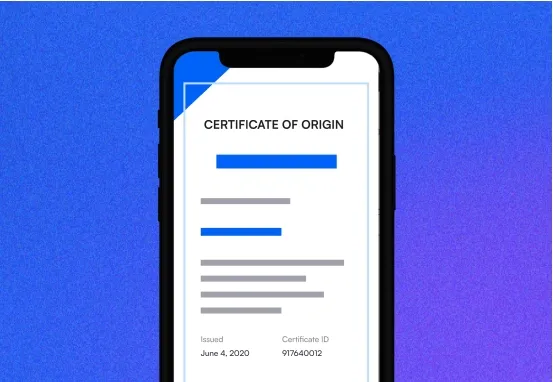
2. Issue
Every product document you issue will automatically become a fraud-proof, high-security digital certificate. Dock places a unique cryptographic signature inside each document, making it impossible to fake.

3. Verify
Your users receive the documents and store them in a secure digital wallet app. Your stakeholders, from their verification portal or digital wallet app, will request what documents they need from users, and the authenticity of the data is instantly verified.

Dock is far easier to use than many of the existing tools out there. It can deploy very quickly and it will be very easy for our developers to use the tool.



Create your first Reusable Digital ID today
Turn verified ID data into Reusable Digital ID Credentials, instantly verify their authenticity and get paid when they are verified by third parties.





